Design, Verify, & Generate Code for Cryptographic Protocols
Rapidly prototype and deploy secure protocols without needing to be a cryptography expert
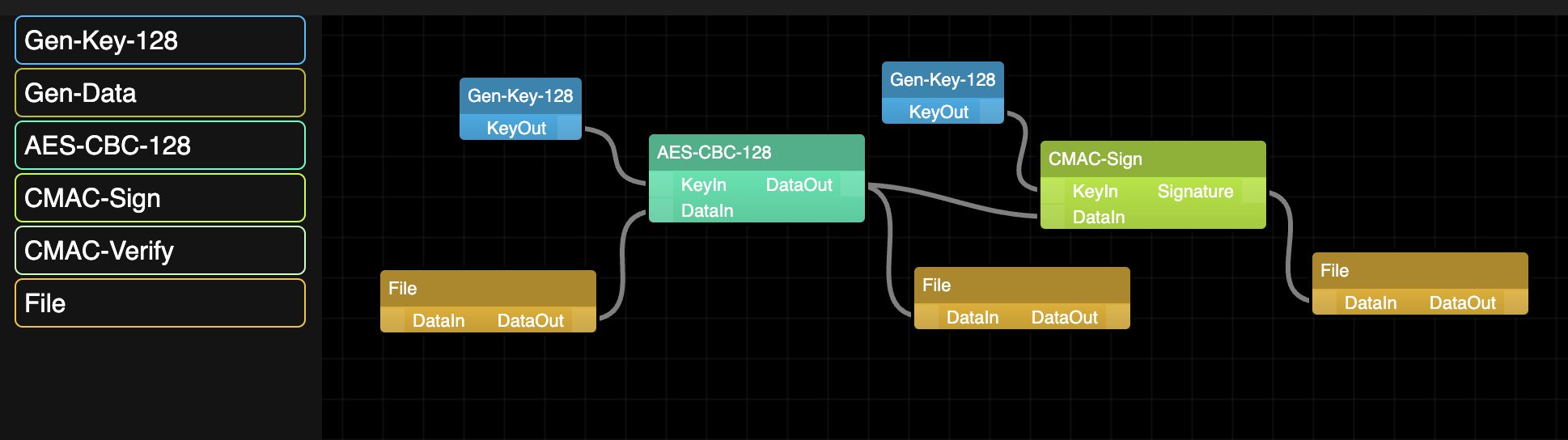
Graphical Modelling
Graphical Language for Cryptography Protocol Engineering
Graphical Language
Drag and drop cryptographic primatives and connect them to form your protocol.
Automatic Validation
Prevent incorrect and invalid use of cryptographic primitives and insecure data flows.
Code Generation
Generate secure C code targeting supported HSMs and cryptographic libraries.
Supports PKCS#11
Implement and prototype protocols that conform to PKCS#11.
End-To-End Workflow
Design To Deployment
01
Design
Drag and drop cryptographic primitives and connect them to form the protocol.
02
Qualify
Validate the security and correctness of the protocol and verify integration with existing systems.
03
Generate Code
Generate secure implementations of the protocol targeting supported HSMs and cryptography libraries.
04
Deploy
Deploy and integrate the generated libraries into your applications.
Subscribe To Our Blog
Follow our latest news and articles: